Configuring DKIM in SpamTitan Gateway
Go to System Setup > Mail Relay > DKIM. The table shows a list of your domain relays.
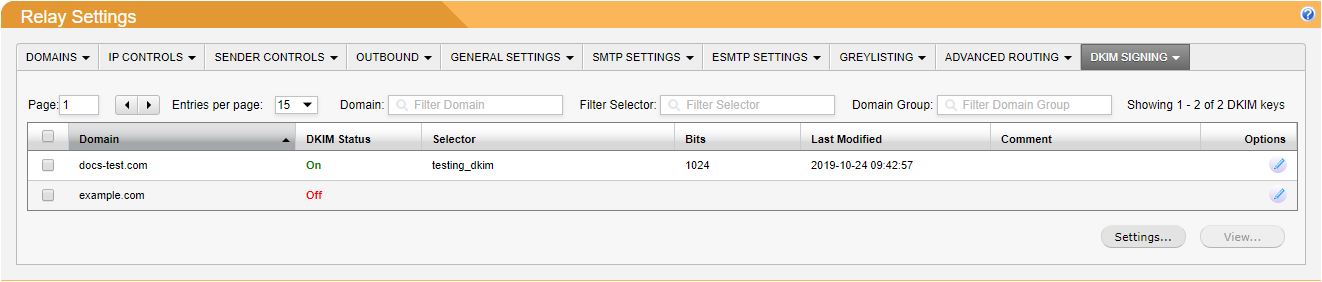
Click the edit
 icon beside a domain and the DKIM:your_domain window displays.
icon beside a domain and the DKIM:your_domain window displays.Go to the DOMAIN KEY tab.
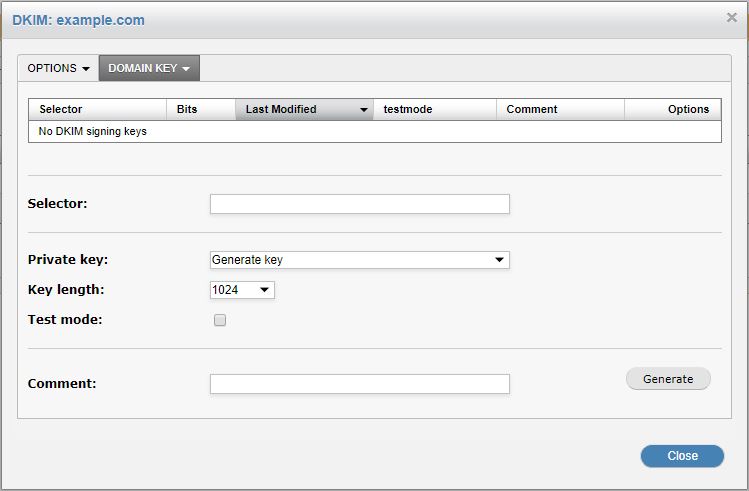
In the Selector: field, enter a selector name. This can be anything you want. It is used to uniquely distinguish the domain key that SpamTitan uses from any other domain keys you may have.
Important
It is important to periodically rotate your DKIM keys (e.g. every month or every quarter). The longer they are unchanged, the higher the risk of one being compromised.
Optionally, enter these fields:
Private key: A new private key may be used to generate each key pair, or you may use an existing private key if required.
Key length: SpamTitan Gateway can generate 1024-bit or 2048-bit domain keys. Some DNS registrars may not support a longer key length, however, a longer key length is more secure and therefore recommended.
Test mode: Enabling Test mode creates a DNS TXT record that includes a "t=y" field. This indicates to servers verifying the signature that the domain is testing DKIM, and must not treat messages from signers in testing mode differently from unsigned email, even if the signature fails to verify.
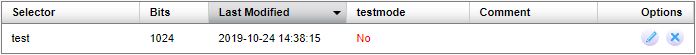
Click Generate. The new domain key will now be listed in the table:
Go to the OPTIONS tab.
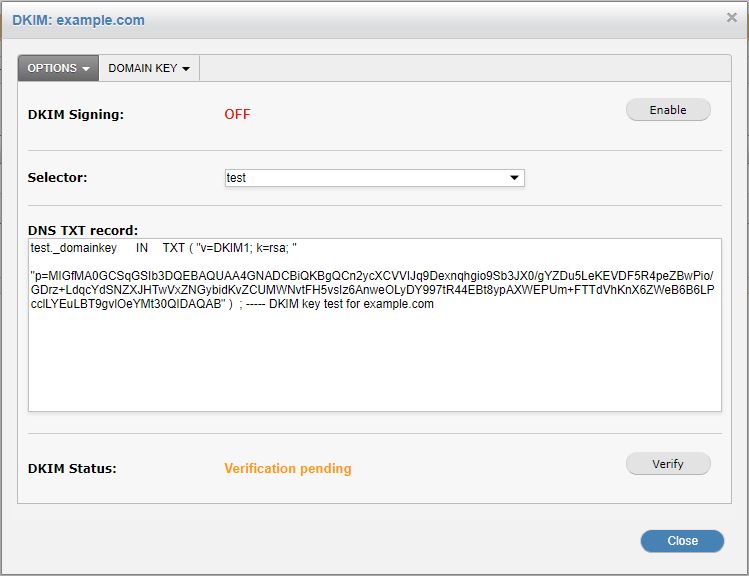
Select and copy the DNS TXT record to a text editor and remove all spaces, carriage returns, and double-quotes. Select and highlight the following only:
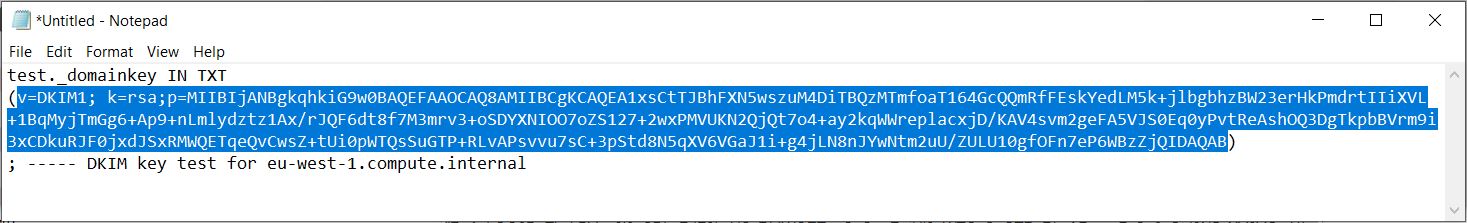
On your DNS server, create a TXT record called selectorName._domainkey.yourdomain. Paste the copied text from step 8 and remove extraneous formatting. It should look similar to this example:
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDj1nxgYYFKNXBqMi/81QS+oG5NklPwtNQxksU3B9sBN8E37+dlGIV+YEjj6cpwBCc0z+RXjTuM6e6wwjBLo/ds9HX654OyBDmwKkyyl0EWgIF8H/UNcTmL2tBln5NxJvygoceJ9FtqLLUVN75PNt74ykZQxMhZEZNY+VPJM/URaQIDAQAB
On your DNS server, create a TXT record called _domainkey.yourdomain. This is the Policy Record.
Go back to the OPTIONS tab and click Verify. If SpamTitan can retrieve the DNS TXT record and if it matches what is specified in SpamTitan, the verification will succeed.
Policy Records
A domain name using DomainKeys should have a single policy record configured. This is a DNS TXT-record with the name _domainkey prefixed to the domain name. For example, _domainkey.example.com.
The record contains the policy, which is either "o=-" or "o=~", where "o=-" means "all e-mails from this domain are signed", and "o=~" means "some e-mails from this domain are signed".
Additional fields for test (t), responsible e-mail address (r), and notes (n) may also be included, for example, "o=-; n=some notes".
Example: "o=-;r=postmaster@yourdomain.com;n=somenotes"
Once verification has succeeded, click Enable to enable DKIM Signing for this domain.