MS Sentinel Integration
With MS Sentinel, you can configure Playbooks (logic apps) in Azure that will run in response to a particular alert or event. With these Playbooks, an activity can be configured to forward the alert information to the Azure Orchestrator (On-Premise setup is not currently compatible with MS Sentinel). This activity will act like a webhook.
Two items of information that need to be forwarded to the Orchestrator are an identifier for the alert that has occurred and an identifier for the user. The identifier for the user must be the user Azure AD username. The Orchestrator integrates with the customer Azure AD and uses the username as a lookup value to get the correct email address (SafeTitan portal username). This information is used to locate the offending user in the SafeTitan instance and the Alert subscription so that the correct response can be coordinated.
When configuring the Playbook, create an HTTP Post activity, as shown in this example:
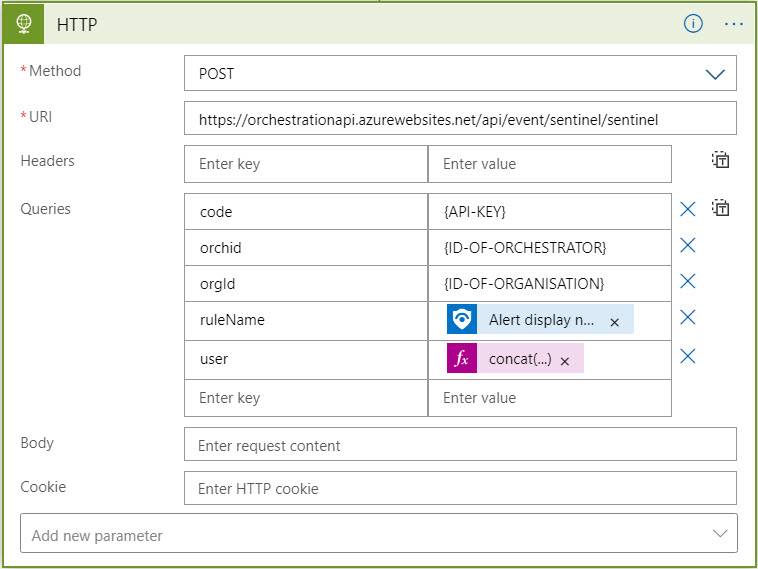
The setup above contains the URL that the event information is to be forwarded to. It also contains the properties identifying the correct Orchestrator, organization, offending user, and rule/alert that was triggered. Depending on how you have configured your alerts/rules, these user details and alert name are extracted differently. In the example above, the rule name is taken from the Alert Display name attribute.
Note
This must be an identical match for the name of the subscription created in your Safetitan portal (see documentation on setting up Realtime events and response).
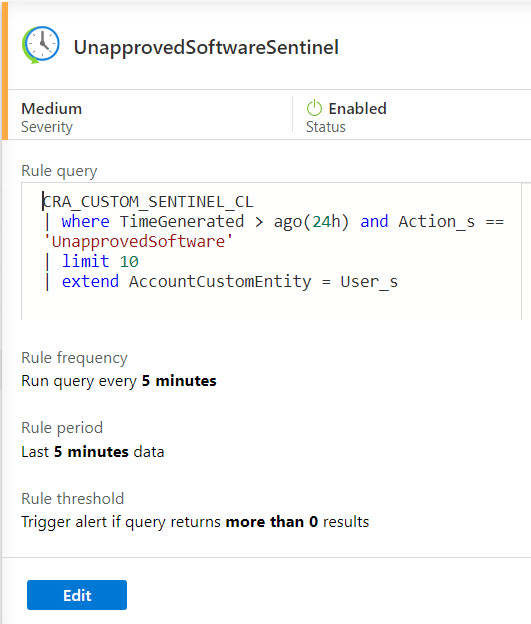
It is also important to note that MS Sentinel does not fire these events at real time. The poll for the events is based on the timeframe you provide in your alert setup. In the example below, the logs are polled every 5 minutes.